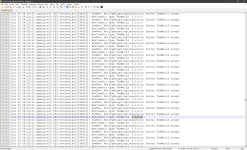
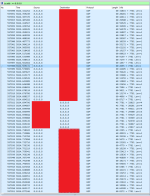
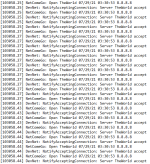
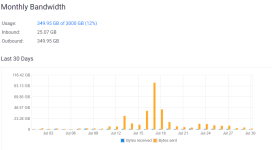
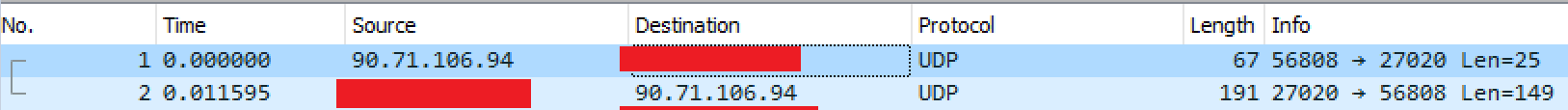
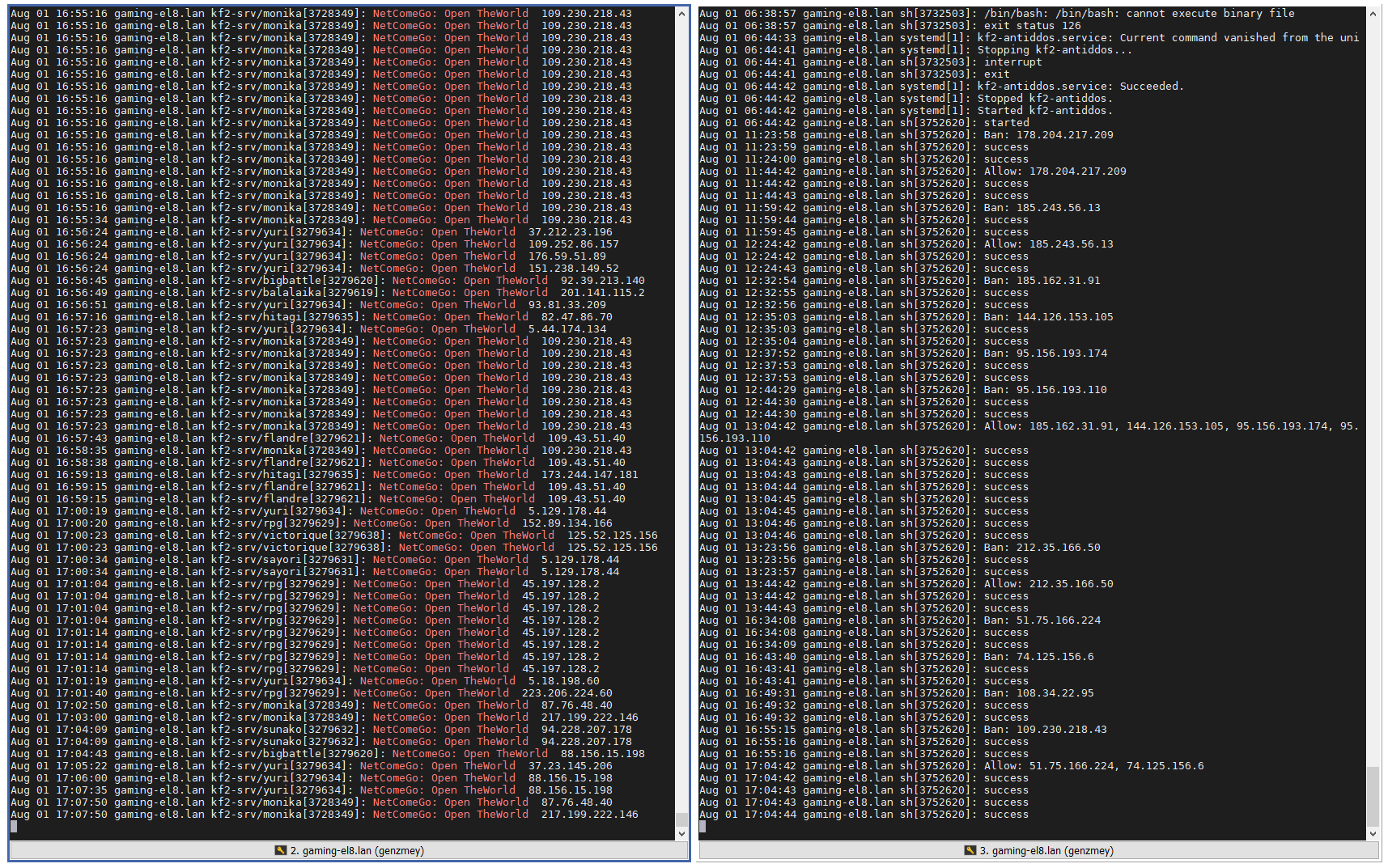
Well, yeah. So it increasingly looks like changing the default port doesn't help long term.
Theoretically, the port your server listens on is discoverable via Steam Client or maybe also via Steam API, so it shouldn't be a big deal to run a discovery and then attack what's discovered. The reason why changing the port at least temporarily stops the attack is probably because the discovery is run once in a while, so if you changed the port, the attack stops until the next discovery event happens and your server ends up in the list of the ones the dude wants to attack at the moment. Then, again, theoretically, immediately changing the port after the attack is detected should again stop it until the next discovery event, so, theoretically one can develop a script that detects the attack, stops the server (if noone's playing), changes the port to some random value, starts the server. The downside is the server gets removed from the favorites tab and also it's temporary and one will need to keep changing it making the favorites functionality useless for his users.
It is unclear why TWI said that they aren't under attack. Aren't they really? Or their pipes are so big that they just don't care about traffic, they don't have NG firewalls that would start dropping it and their servers don't hang up? It's unlikely IMO given what we know that it's TWI themselves behind the attack (although so far it seems that only the community servers are affected) as it's a criminal offense and one would think the company wouldn't risk doing that.
I'm actually lost at guessing the motives of someone behind the attacks. I've heard that it's very typical, say, in Minecraft scene to DDoS the servers of one's competitors. It kind of makes some sense at least. Could it be the motive here? Say, some rather big community servers owner tries to knock down his competitors. Kind of ridiculous to me, but that's what happens in the Minecraft scene. E.g.:
Minecraft is big money.

www.businessinsider.com
Could very well be a typical journo BS, hard to tell. But hey, maybe I should start thinking about providing a DDoS KF2 hosting services or DDoS KF2 protection consulting services.