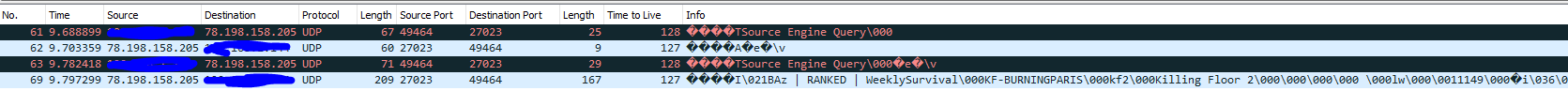
So i have switch again to slightly better solution. In the log files you can find lines like this which can be phrased out to get the client ip address. This allows us to create a whitelist of known clients using a ipset.
My ip tables setup now looks like:
Allow existing(RELATED,ESTABLISHED) game sessions -> rate limit total packets to 600 / second per ip
Allow known client new session(ipset) -> rate limit to 20 NEW connections / second per ip address
Allow unknown client new session -> rate limit to 20 connections / second for the subnet /8. This subnet can probably be made larger if you have been adding client ip addresses to the ipset whitelist for a while.
Code:iptables -I FORWARD 1 -p udp -m conntrack --ctstate RELATED,ESTABLISHED -m udp --dport 7778:7779 -j GAME-RATE-LIMIT iptables -I FORWARD 6 -p udp -m conntrack --ctstate NEW -m udp --dport 7778:7779 -m set --match-set KNOWN-CLIENT-RATE-LIMIT -j NEW-GAME-RATE-LIMIT iptables -I FORWARD 7 -d <KF2 server ip> -p udp -m udp --dport 7778:7779 -m connlimit --connlimit-above 20 --connlimit-mask 8 --connlimit-saddr -m limit --limit 1/sec --limit-burst 1 -j LOG --log-prefix "Drop-Connection-Limit: " iptables -I FORWARD 8 -d <KF2 server ip> -p udp -m udp --dport 7778:7779 -m connlimit --connlimit-above 20 --connlimit-mask 8 --connlimit-saddr -j DROP iptables -I FORWARD 9 -p udp -m conntrack --ctstate NEW -m udp --dport 7778:7779 -j ACCEPT
ipset
Code:ipset create KNOWN-CLIENT-RATE-LIMIT hash:net family inet hashsize 32768 maxelem 655360 ipset add KNOWN-CLIENT-RATE-LIMIT 10.0.0.1 ipset add KNOWN-CLIENT-RATE-LIMIT 10.0.0.2 ipset add KNOWN-CLIENT-RATE-LIMIT 10.0.0.3
This works well. It stops any false positives from known clients.
Note: To optimize your firewall rules and reduce CPU load / latency all frequently used rules like RELATED,ESTABLISHED statements should be at the beginning of your firewall rules. All firewall rules using ipset should be as close to the bottom of the firewall rules as possible to reduce the number of packets that they have to do a lookup on. I did a small test on a VM with 2 cores and a ipset rule with 655360 lines. I was able to put a gigabit of traffic through the server with 60-75% CPU usage.
Edit diagram didn't upload first time:
View attachment 2337216
Hey everybody,
It happened last week for the first time when my server started acting weird (teleporting around the map, player pings jumping like crazy etc).
So I reinstalled the server, moved it to windows for testing purpose etc
Of course nothing helped and I'm very glad that I found this thread.
For now I'm using GenZmeY's anti ddos solution which does it's job so far.
Thanks for that tool GenZmeY, we can play again
However he highly recommends using bazztheallmighty's solution but that's a bit too much for me.
So I asked a few friends who are "quite good" with linux and their reaction was "oh no, this is complicated af and doesnt seem to be a tutorial"
So maybe someone can help setting this up.
Saw you can buy whole books about that iptable stuff...oh boy :|
I also tried to contact you baz, but even when I just want to check your profile I receive "permission denied..."
Im on the latest Ubuntu Server
Thank you
Upvote
0