EDIT: From further reading, it's sounding like I may have been receiving traffic from these IPs in an attempt to max out connection limits on the server, and the response traffic is much greater than the inbound traffic - a sort of amplification attack. I sadly don't have any network dumps from the attack period to confirm that myself.
Hey,
It's good to see I'm not alone in this issue.
Back on Tuesday, my server hosted with Kimsufi (OVH) was shut down by an automatic process that considered my server to be hacked. The logs they provided showed a very large number of UDP packets originating from my KF2 server to a singular IP address. Their statistics showed 140,000 packets per second, and about 68 Mbps of bandwidth.
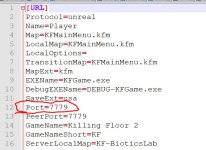
I've included a screenshot from their ticket here:

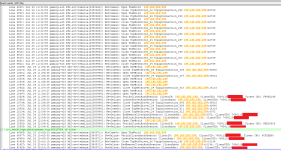
It's taken me until last night to finally get access to my data (long, irrelevant story), and I've been having a look through my Launch.log. I'm seeing basically the same as what's already been posted in terms of log entries. Many thousands of "NotifyAcception Connection", followed by timeouts.
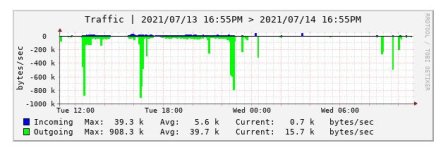
However, based on my own stats, it doesn't look like my server was the victim of a DDoS, but rather all of the traffic was OUTBOUND, so it looks like my server had actually become the attack vector. I've included a screenshot below of the network monitoring showing the traffic all being outbound. This matches the information OVH provided:
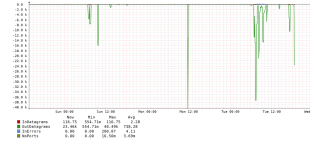
At this time, i'm not sure how somebody is managing to use my KF2 server daemon to generate all of this traffic, as I'm not seeing a high volume of inbound traffic to generate it. I do use FirewallD, so I can potentially try to do something that quickly kills excessive connections to an IP, but it's very much a band-aid fix. I suspect there may be an exploitable flaw in the server software itself.
I did some quick analysis on the destinations for this traffic which i've included below:
grep "NetComeGo: Open TheWorld" Launch.log | sed 's/.* //' | sort | uniq -c | sort -nr
56719 104.153.108.19
51109 199.231.233.15
46622 73.247.224.154
33927 178.237.56.153
30389 12.1.21.1
20091 24.167.129.214
19530 74.74.74.74
15279 73.73.73.73
14309 178.237.56.155
14087 104.153.108.192
9365 80.80.80.80
7627 192.172.226.159
7565 70.177.113.16
5316 50.7.8.131
4591 1.32.42.3
4443 171.33.133.153
3015 68.142.122.37
2748 8.41.7.62
2600 68.185.71.105
1533 45.48.19.195
1510 8.41.7.41
1383 8.44.63.63
871 192.172.226.78
667 8.41.7.56
616 144.172.73.69
564 185.53.90.81
558 172.104.213.248
550 70.70.70.79
500 69.141.13.26
I would be very interested to learn more about what other people have seen though. If somebody could DM me a link to any relevant Discords that would be greatly appreciated. In the meantime, once I've finished recovering my server I think i'll have to unfortunately temporarily disable my KF2 server until I understand more.