Code:iptables -A INPUT -p udp -m udp --dport 7777:7779 -m connlimit --connlimit-above 3 --connlimit-mask 20 --connlimit-saddr -j DROP
This does not work for me.
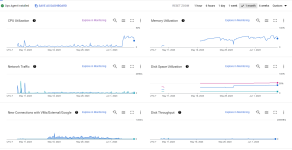
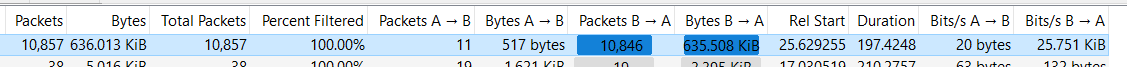
I'm not sure why the -m (match) option is here, check with baz. I don't use it and it works. Check that your servers are indeed listening on ports that are being defended here (netstat -plunt). Check your iptables is installed and functional. Check if the rules were indeed added by checking the appropriate chain. There was also a command shared a few pages back that used the "watch" command to see how the packets go through the rules in real time, you should see the numbers there if it works.
Upvote
0